Our approach: unified data-centric protection
Gain the most complete visibility into your end-to-end data risk exposure
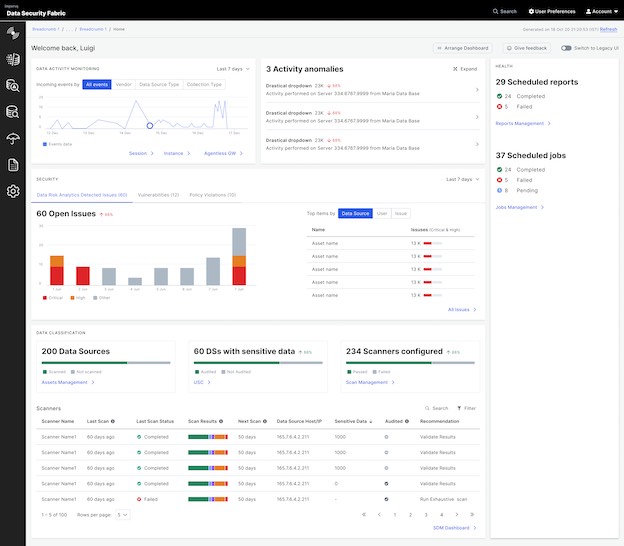
Imperva Data Security Fabric (DSF) provides over 260 built-in integrations with other widely used enterprise security infrastructure systems–including traditional SIEM solutions, CMDB tools, enterprise SOAR platforms, web application firewalls, and more.
Our approach is to unify the protection of data by taking a “data-centric” approach to security. Imperva’s strategy means that we provide a single, unified view of all data security events across your entire organization, regardless of where the data resides or what security tools are currently being used to protect it.
With this visibility into your data, you can start taking control of user access, organizational processes, and application security–while enabling disparate IT teams with, heretofore siloed and inconsistent access to data stores, the ability to unlock new business innovations and insights.

Data-level SOAR integration: built-in playbooks offer a mature approach to data breach prevention
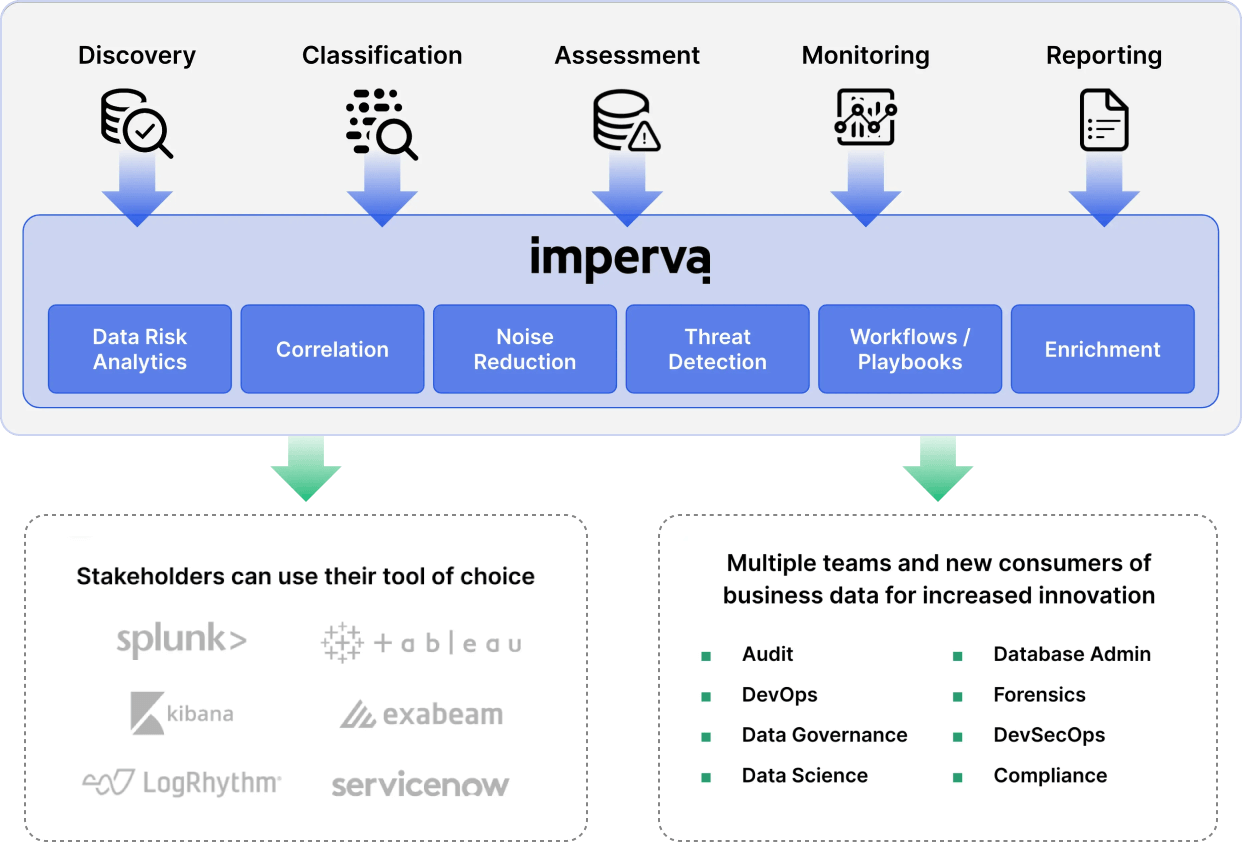
Traditional data activity monitoring and logging tools flood security operations center (SOC) teams with low-value data and alerts, creating a significant data security challenge for organizations. An excess of low-confidence information can give rise to bottlenecks in event-level workflow communications as SOC teams struggle to prioritize alerts for remediation and decide which anomalous events warrant investigation. Manual steps are often required to enter these incidents into the organization’s Security, Orchestration, Automation, and Response (SOAR) platform, introducing more delays, disorganization, and potential for errors.
With automation provided by Imperva DSF playbooks, you can easily integrate high-value threat alerts with SOAR platforms to streamline and accelerate incident response processes. Imperva Data Risk Analytics (DRA) can automatically detect and classify data security incidents, trigger appropriate actions, and accelerate incident investigation and resolution.


2,000+ SOAR integrations
Imperva DSF can optimize your Splunk installation
Many enterprises use Splunk as the primary repository for native database logging and data activity monitoring (DAM) tools.
These logs can represent a significant amount of the data indexed in Splunk. Storing these logs enables adherence to compliance regulations but is often otherwise unused due to the lack of security context.
Organizations implement Imperva Data Security Fabric (DSF) as a database log pre-processor to Splunk to increase the value of raw logs. Imperva DSF filters, compresses, stores, and indexes the raw event data, making it available in Splunk via virtual indices. Analytics within Imperva DSF bridge user identity, data sensitivity, and attack detection, meaning that threat alerts include rich technical context and detection timelines. Security analysts have bidirectional access for interactive data exploration.
This approach enables organizations to increase the security value of their Splunk deployment and markedly reduces Splunk ingestion and development costs.
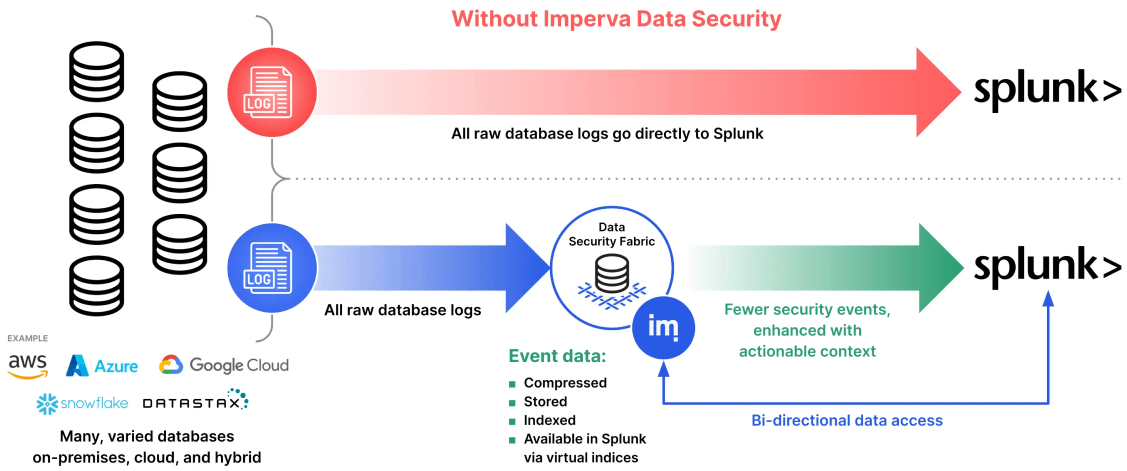
How it works
Native logs from on-premises and cloud data repositories are forwarded to Imperva Data Security Fabric for pre-processing. Imperva enriches the information with context into users, access, and threats. Only the intelligence extracted from raw data is forwarded to Splunk, allowing Splunk to remain effective at incidence response and enterprise-level event correlation.
Imperva Data Security Fabric protects all data types with a single system that delivers multiple business capabilities
Imperva Data Security Fabric is the first data-centric solution that enables your organization's security and compliance teams to quickly and easily secure sensitive data no matter where it resides with an integrated, proactive approach to visibility and predictive analytics.
Imperva Data Security Fabric is composed of cutting-edge orchestrated technical capabilities that work in unison to protect your data across your entire organization:
Data Discovery & Classification
Discover ungoverned data, classify all data, and assess vulnerabilities.
Learn moreData Activity Monitoring
Gain complete visibility and ensure compliance with continuous monitoring, auditing and analyzing all data store and data types.
Learn moreData Retention & Archive
Meet any data archiving requirement using the most cost efficient storage technology available.
Learn moreData Risk Management
Detect and report non-compliant, risky, or malicious data access behavior across all of your data repositories enterprise-wide to accelerate remediation.
Learn moreEcosystem Integrations
Enhance the value of your existing technology investments - for both incident context and additional data capabilities.
Learn moreData Encryption & Tokenization
Protect critical data with encryption, key management, and tokenization wherever it resides.
Learn moreStatic Data Masking
Modify sensitive data so it is of no value to unauthorized users while still being usable by your systems.
Learn moreAutomated Workflows & Playbooks
Achieve higher scale and increase DevOps efficiency through the use of automated workflows delivered through trusted repositories.
Learn moreSensitive Data Management
Identify, locate, classify, and secure sensitive data across various data stores located either on-premises or in the cloud.
Learn more